Find out how SemiAntiVirus.vbs has come into your machine and how to delete it
Errors that can be possibly shown after you (or Anti Virus Software) delete SemiAntiVirus.vbs
Read the script of SemiAntiVirus.vbs
and here in this post, I will tell you how to fix the errors
Fixing the Windows Script Host Error which puts up a pop up window at the start up saying "cannot find script file c:windows\system32\semiantivirus.vbs"
Reasons
This happens because the virus is coded to launch with the userinit.exe which manages the start up sequences at the start up.
When the computer boots, userinit.exe is executed and then, it looks for the semiantivirus.vbs to execute. But we (or the anti virus software) have deleted the semiantivirus.vbs in this step.
Since the computer cannot find the semiantivirus.vbs file it displays the above pop up window
So, first, you have to break the link between the userinit.exe and semiantivirus.vbs
Fix
1.Open Registry Editor (Start-->Run-->regedit-->OK)
2. Go to HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion and select \Winlogon
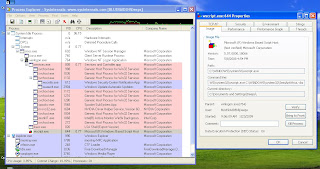
3. On the right side pane, you will see a long list of entries. Out of them, right click on userinit and select Modify
4.In the Value Data text box, you will see something like C:\WINDOWS\system32\userinit.exe,c:windows\system32\semiantivirus.vbs
5. Modify the value to C:\WINDOWS\system32\userinit.exe and click ok (then, the userinit registry entry should look like this. Look at the status bar for navigation details)
6. Close the registry editor and restart the computer

--OR--
If you like to do it in the command prompt this is the command reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v Userinit /d %%SYSTEMROOT%%\System32\userinit.exe, /f
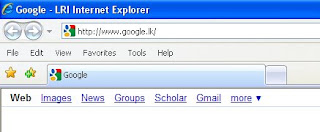
Fixing the Internet Explorer
Reasons
It looks like this because the virus has edited the registry entries for the Title bar and the Home Page
Fix for the Title Bar
1.Open Registry Editor (Start-->Run-->regedit-->OK)
2.Go to HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer and select main
3. On the right side pane, you will see a long list of entries. Out of them, right click on Window Title and select Modify
4. Under Value Data, you will see LRI Internet Explorer. Change that to Internet Explorer and click ok
--OR--
If you would like to do it in the command prompt, this is the command reg add "HKCU\Software\Microsoft\Internet Explorer\Main" /v "Window Title" /d "" /f
Fix for the Home Page
1. Repeat the 1 and 2 steps of the Fix for the Tiltle Bar
2.On the right side pane, right click on Start Page and select Modify
3. Fill in the Value Data box with the URL of the page that you wish to have as your home page(For example,www.google.lk) and click ok
--OR--
If you would like to do it in the command prompt this is the command reg add "HKCU\Software\Microsoft\Internet Explorer\Main" /v "Start Page" /d "http://www.google.lk/" /f
--OR--
Do it simply in the settings of Internet Explorer
1.Go to Tools-->Internet Options-->General-->Home Page
1.Go to Tools-->Internet Options-->General-->Home Page
After completing above steps, the registry entry for Internet Explorer should look like this(look at the status bar for navigation details)
 All the changes would be visible after you restart Internet Explorer
All the changes would be visible after you restart Internet ExplorerCompleting the above steps should remove the implications of the semiantivirus.vbs attack on your computer.
And thank you Shaakunthala, Sadeepa, Isuru and Abish for your valuable comments in earlier posts!!